bittorrent客户端最初是如何发现其对等点的?
当你的torrent客户端加入swarm来共享和收集文件片段时,它如何确切地知道所有的对等点在哪里?请继续阅读,我们将深入了解支撑BitTorrent协议的机制。
今天的问答环节是由SuperUser提供的,SuperUser是Stack Exchange的一个分支,是一个由社区驱动的问答网站分组。
问题
超级用户读者Steve V.对BitTorrent协议中的分布式哈希表(DHT)系统有一个非常具体的问题:
I’ve already read this SuperUser answer and this Wikipedia article but both are too technical for me to really wrap my head around.
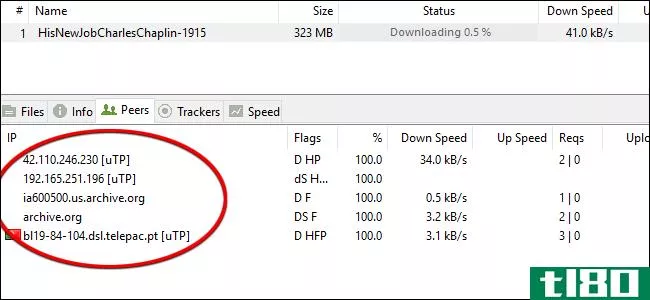
I understand the idea of a tracker: clients connect to a central server which maintains a list of peers in a swarm.
I also understand the idea of peer exchange: clients already in a swarm send the complete list of their peers to each other. If new peers are discovered, they are added to the list.
My question is, how does DHT work? That is, how can a new client join a swarm without either a tracker or the knowledge of at least one member of the swarm to exchange peers with?
(Note: simple explanati*** are best.)
他的问题反过来又引发了一个关于BitTorrent系统不同功能的非常详细的回答;现在让我们来看看。
答案
超级用户贡献者Allquixotic提供了一个深入的解释:
How can a new client join a swarm without either a tracker or the knowledge of at least one member of the swarm to exchange peers with?
You can’t. It is impossible.*
* (Unless a node on your local area network happens to already be a node in the DHT. In this case, you could use a broadcasting mechani**, such as Avahi, to “discover” this peer, and bootstrap from them. But how did they bootstrap themselves? Eventually, you’ll hit a situation where you need to connect to the public Internet. And the public Internet is unicast-only, not multicast, so you’re stuck with using pre-determined lists of peers.)
References
Bittorrent DHT is implemented via a protocol known as Kademlia, which is a special case of theoretical concept of a Distributed hash table.
Exposition
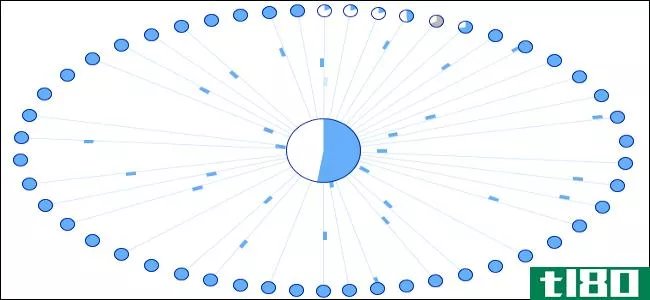
With the Kademlia protocol, when you join the network, you go through a bootstrapping procedure, which absolutely requires that you know, in advance, the IP address and port of at least one node already participating in the DHT network. The tracker that you connect to, for instance, may be itself a DHT node. Once you are connected to one DHT node, you then proceed to download information from the DHT, which provides you connectivity information for more nodes, and you then navigate that “graph” structure to obtain connecti*** to more and more nodes, who can provide both connectivity to other nodes, and payload data (chunks of the download).
I think your actual question in bold — that of how to join a Kademlia DHT network without knowing anyother members — is based on a false assumption.
The simple answer to your question in bold is, you don’t. If you do not know ANY information at all about even one host which might contain DHT metadata, you are stuck — you can’t even get started. I mean, sure, you could brute force attempt to discover an IP on the public internet with an open port that happens to broadcast DHT information. But more likely, your BT client is hard-coded to some specific static IP or DNS which resolves to a stable DHT node, which just provides the DHT metadata.
Basically, the DHT is only as decentralized as the joining mechani**, and because the joining mechani** is fairly brittle (there’s no way to “broadcast” over the entire Internet! so you have to unicastto an individual pre-assigned host to get the DHT data), Kademlia DHT isn’t really decentralized. Not in the strictest sense of the word.
Imagine this scenario: Someone who wants P2P to stop goes out and prepares an attack on all commonly used stable DHT nodes which are used for bootstrapping. Once they’ve staged their attack, they spring it on all nodes all at once. Wham; every single bootstrapping DHT node is down all in one fell swoop. Now what? You’re stuck with connecting to centralized trackers to download traditional lists of peers from those. Well, if they attack the trackers too, then you’re really, really up a creek. In other words, Kademlia and the entire BT network is c***trained by the limitati*** of the Internet itself, in that, there is a finite (and relatively **all) number of computers that you would have to successfully attack or take offline to prevent >90% of users from connecting to the network.
Once the “pseudo-centralized” bootstrapping nodes are all gone, the interior nodes of the DHT, which are not bootstrapping because nobody on the outside of the DHT knows about the interior nodes, are useless; they can’t bring new nodes into the DHT. So, as each interior node disconnects from the DHT over time, either due to people shutting down their computers, rebooting for updates, etc., the network would collapse.
Of course, to get around this, someone could deploy a patched BitTorrent client with a new list of pre-determined stable DHT nodes or DNS addresses, and loudly advertise to the P2P community to use this new list instead. But this would become a “whack-a-mole” situation where the aggressor (the node-eater) would progressively download these lists themselves, and target the brave new bootstrapping nodes, then take them offline, too.
我们不仅了解了原始问题的答案,还了解了BitTorrent系统的本质及其漏洞。
有什么要补充的解释吗?在评论中发出声音。想从其他精通技术的Stack Exchange用户那里了解更多答案吗?在这里查看完整的讨论主题。
- 发表于 2021-04-11 19:09
- 阅读 ( 171 )
- 分类:互联网
你可能感兴趣的文章
p2p(peer-to-peer)文件共享的工作原理
...zaa和Gnutella网络上获得(其中Limewire可能是最著名的Gnutella客户端)。 ...
- 发布于 2021-03-23 12:39
- 阅读 ( 303 )
为大家准备的torrent指南
...际文件和共享它的人的信息。它就像一个地图,BitTorrent客户端使用它将所有的部分组装在一起。 ...
- 发布于 2021-03-25 04:47
- 阅读 ( 296 )
免费下载的5个最佳torrent客户端(utorrent备选方案)
... 最好的torrent客户端是qBittorrent。以下是该应用程序的一些关键功能: ...
- 发布于 2021-03-25 19:08
- 阅读 ( 287 )
torrent定义:什么是torrent,如何使用它?
... 您主要通过BitTorrent客户端与BitTorrent协议交互,例如qBittorrent,这是uTorrent的最佳替代方案。 ...
- 发布于 2021-03-30 18:54
- 阅读 ( 369 )
我的isp怎么知道我在使用bittorrent?
...使用BitTorrent,也不能知道你正在下载什么。大多数torrent客户端都有某种形式的加密,这使得ISP(和您的家庭路由器)很难锁定BitTorrent流量。不过,他们有一些方法可以判断您正在使用BitTorrent下载某些内容。 下载torrents显示出...
- 发布于 2021-04-02 22:48
- 阅读 ( 223 )
为什么你不能阻止路由器上的bittorrent
...的流量。一些BitTorrent跟踪器禁止使用这些端口的BitTorrent客户端连接,理由是这些客户端可能会降低swarm的整体****。 即使在那个年代,任何人都可以将BitTorrent客户端使用的端口更改为另一个端口,从而逃避禁令。现在更难了。...
- 发布于 2021-04-02 23:58
- 阅读 ( 135 )
什么是新的版权警报系统,它对您有何影响?
...盗版。CCI在YouTube视频中解释了他们的系统: 监控侵权bittorrent群集 BitTorrent本身不提供任何隐私。由于BitTorrent的工作方式,每个从BitTorrent下载文件的人都会将相同文件的片段上传到其他下载者。一个名为MarkMonitor的组织监视人...
- 发布于 2021-04-08 09:29
- 阅读 ( 192 )
mac上传输的最佳替代方案
传输一直被认为是Mac最好的BitTorrent客户端之一,但最近它的服务器出现了背靠背的妥协。如果你担心传输的安全性,这里有一些其他很好的选择。 2016年3月,Tran**ission的服务器遭到破坏,官方Mac版本的Tran**ission包含勒索软件。...
- 发布于 2021-04-08 23:25
- 阅读 ( 155 )
windows上utorrent的最佳替代方案
还记得乌托伦特什么时候很棒吗?新贵的BitTorrent客户端非常轻量级,击败了其他流行的BitTorrent客户端。但那是很久以前的事了,在BitTorrent,Inc.收购uTorrent并在其中塞满垃圾软件和欺诈广告之前。 去他的。不管你是需要下载一...
- 发布于 2021-04-08 23:55
- 阅读 ( 156 )
bittorrent是如何工作的?
...务器。 传统上,计算机通过将.torrent文件加载到BitTorrent客户端来加入BitTorrent群。BitTorrent客户端与.torrent文件中指定的“跟踪器”联系。追踪器是一个特殊的服务器,用来跟踪连接的计算机。追踪器与群中的其他BitTorrent客户端...
- 发布于 2021-04-09 04:38
- 阅读 ( 188 )